Side Channel analysis on Biometric systems
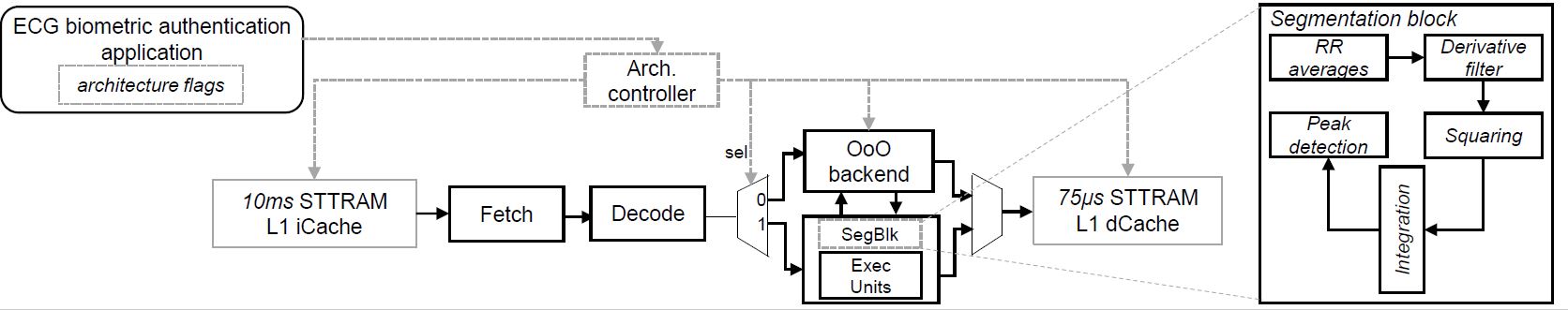
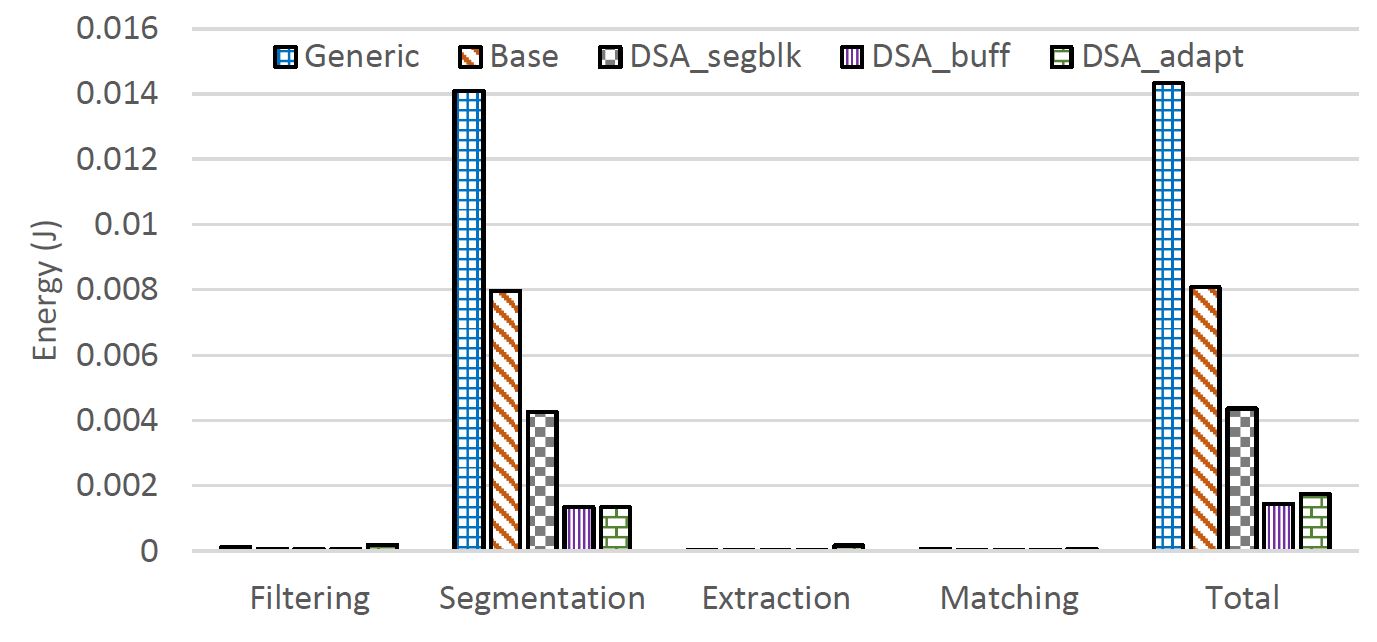
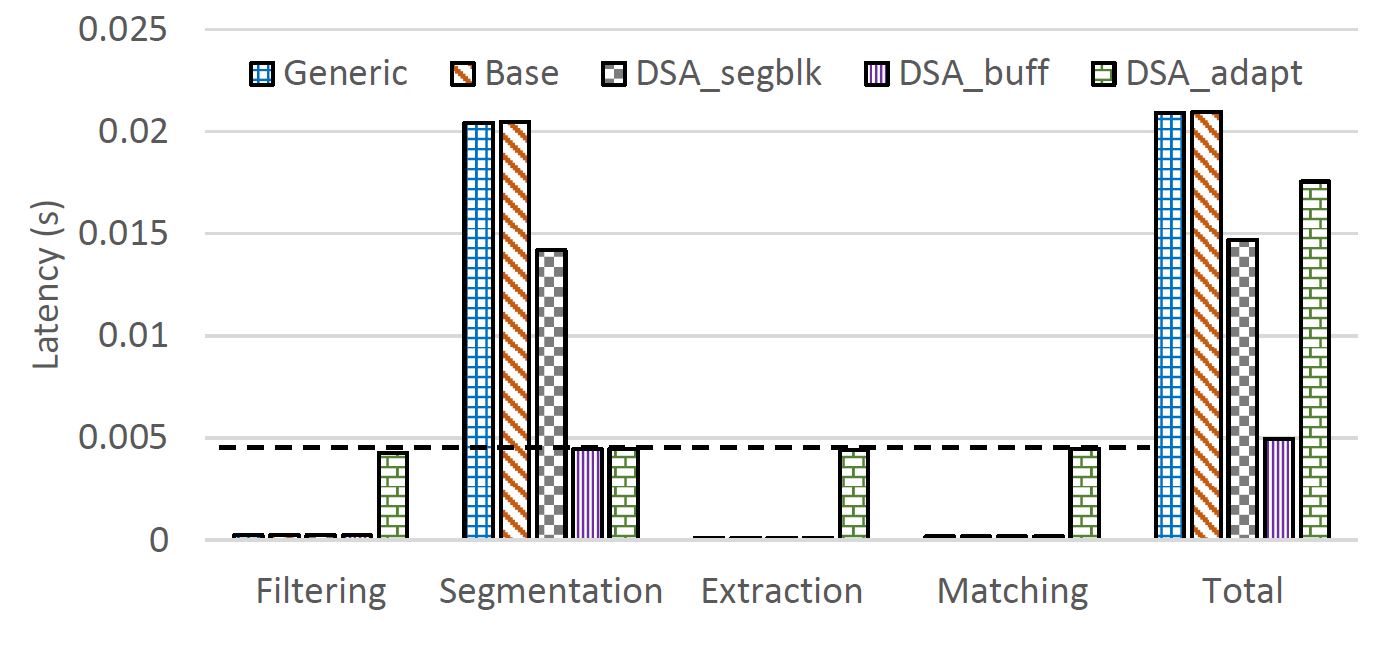
Side-channels are physical signatures/leakages from the execution time, power consumption, and electromagnetic emanations (EM) released while the device is manipulating data. Timing based side-channel leakage, within the context of EBA, occurs when an attacker obtains the execution time of the target authentication step (e.g., filtering, segmentation, feature extraction) for the provided input. The side-channel information can then be analyzed to infer private information. These side-channel attacks rely on the attacker’s ability to detect the variability between different operations or inputs to the system. In this project, we focus on the timing leakage of each step of the ECG-based biometric (EBA) system based on their execution latency. Since different steps of the EBA take different amounts of time, attackers may infer the current steps of the authentication process, or even the specific instructions being executed, simply by monitoring the latency of executions. Therefore, our approach is to ameliorate the timing side-channels by ensuring that the timing information from latency profiles can not be used to infer the operations being performed; thus, reducing the vulnerabilities in EBA computing. Our future work involves incorporating mitigation strategies for power attacks.
Hardware Security
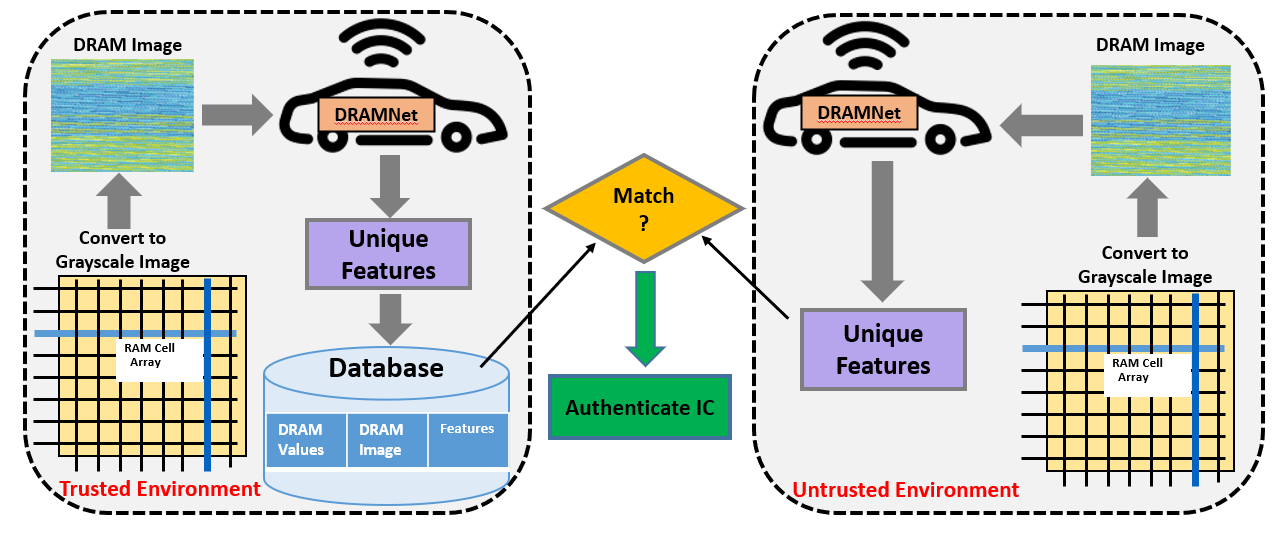
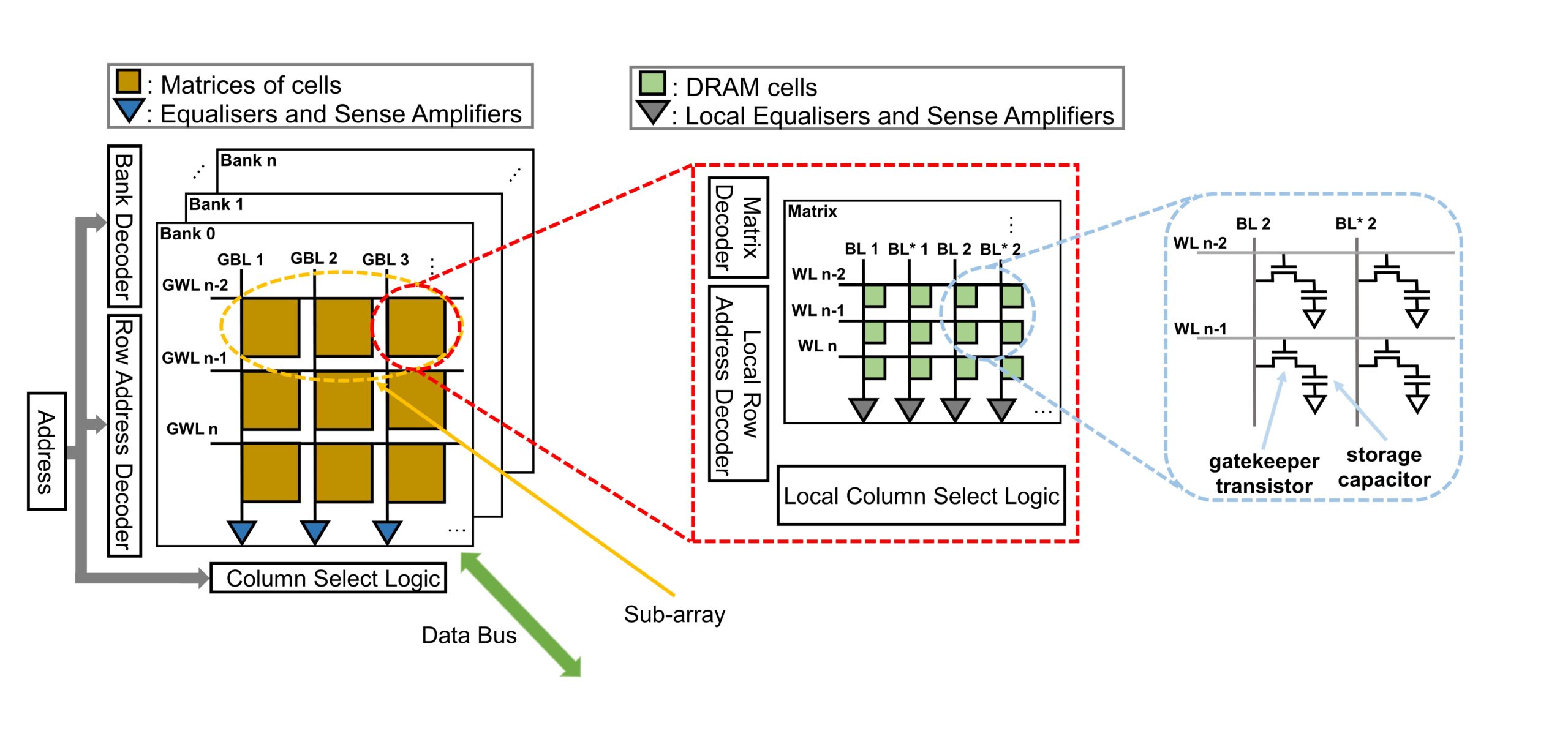
Nowadays, many companies from all over the world are involved in the IC fabrication process to enhance competence and manufacturability due to the complexity of IC design. The abbreviated time-to-market for system-on-chips (SoCs) increases the difficulty by leaving unintentional vulnerabilities in the design. These issues can be exploited by attackers once the microchips are in the field and further lead to more opportunities for adversaries to make malicious inclusions/alterations, information leakage, counterfeiting, piracy activities, adversarial attacks, etc. With increasing security vulnerabilities and trust issues, the Hardware vulnerability continues to become a national and global security threat that impacts the confidentiality, integrity, lifetime, etc. Our research focuses on all security issues such as side- channel, hardware Trojans, IP piracy, reverse engineering, and study hardware security primitives such as PUF, TRNG, Obfuscation.
Authentication for Resource-Constrained Embedded Systems & IoT:
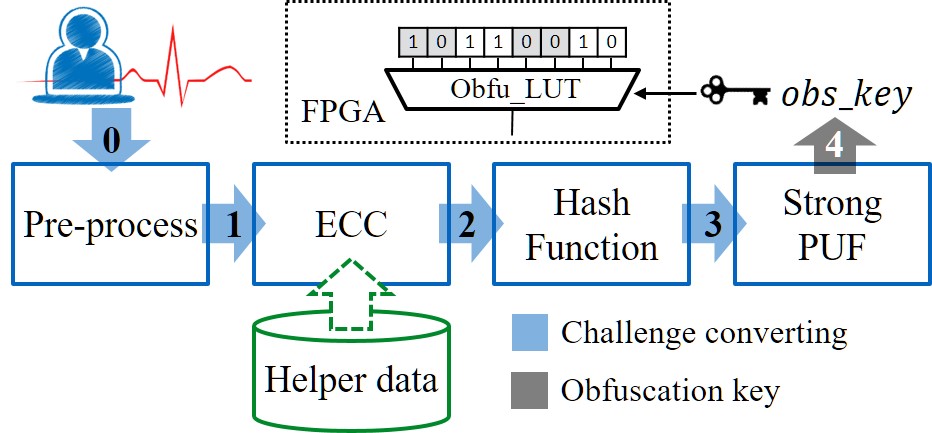
Internet of Things (IoT) has come to denote the widespread deployment of sensors and actuators with ubiquitous interconnectivity, potentially to the Internet, to monitor and control physical systems and critical infrastructure such as smart home, telehealth, smart retail, and autonomous cars. Today, interconnected sensing has pervaded almost every sphere of our lives ushering the dawn of the IoT era. Our homes and appliances are increasingly being made smarter through embedded sensors. Connected wearables and mobile devices allow for continuous remote monitoring of patients and timely administration of medicines but come with risks of fraud – due to the lack of physical presence at the time of collection, the identity of the user that transmits the health information is indeterminate. As people use more IoT devices in daily life and existing access control mechanisms rely heavily on traditional authentication, a new range of security attacks becomes feasible. In fact, with more and more devices sharing data, the value of breaching these systems increases. Thus, addressing the security and privacy issues of the IoT and other connected systems has now become more important than ever. To address these issues, we propose a new promising authentication framework which combines biometrics and physically unclonable functions (PUFs) and hardware obfuscation that can be used to secure multiple IoT devices.
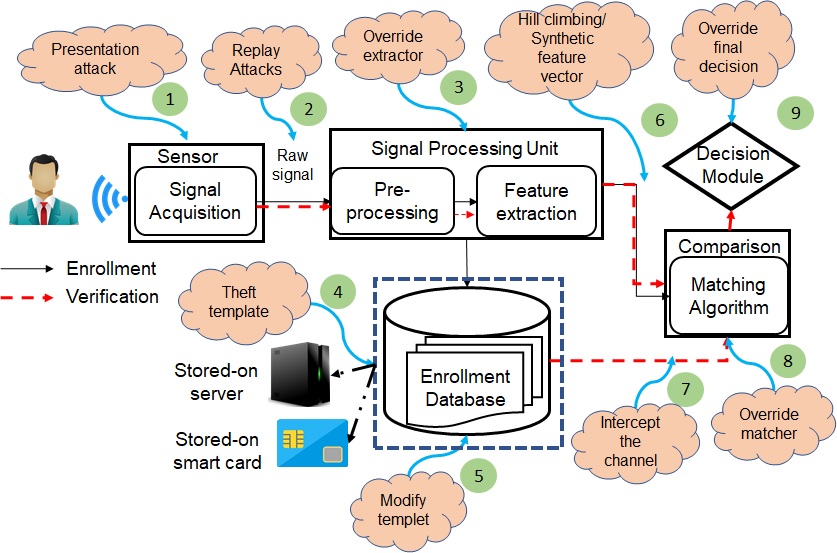
Biometric Presentation Attacks
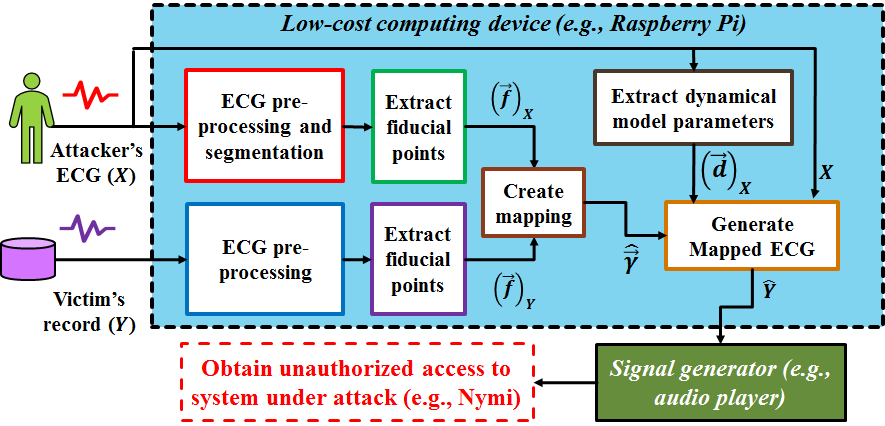
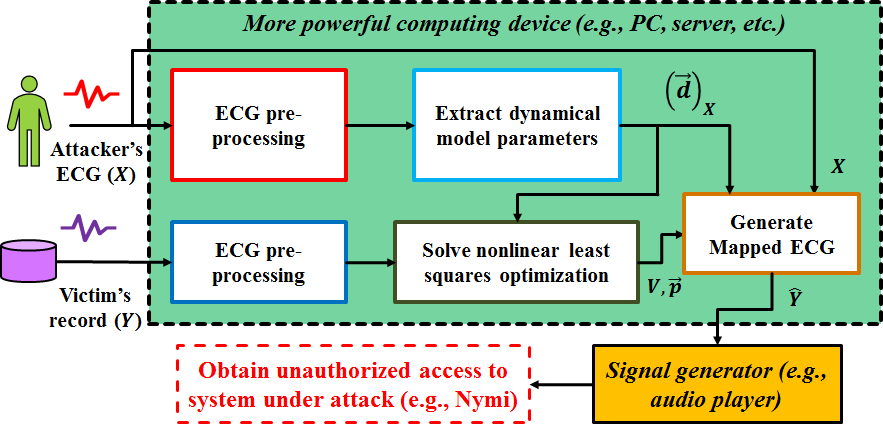
This project addresses the problem of presentation attacks against cardiovascular authentication systems. Cardiovascular authentication systems attempt to recognize individuals based on analyzing relative distances between points and the duration of heartbeat intervals. The resistance of ECG to presentation attacks is often highlighted as one of its major benefits for biometric authentication. However, it is possible for an adversarial user to circumvent the system by presenting an intentionally modified ECG waveform a synthetic ECG signal. These are called presentation attacks. To evaluate vulnerability of cardiovascular recognition, we develop a novel presentation attack where a short template of the victim’s ECG is captured by an attacker and used to map the attacker’s ECG into the victim’s which we call it “cross-subject attacks”. In addition, we propose a mapping function that allows attacker to spoof the ECG based authentication system with data collected on a different device and we call this “cross-device attack”. To detect such attacks, we develop countermeasures techniques from the nature of ECG signal such as heart rate variability and noise that can determine if an input ECG signal corresponds to an attack or not. We were able to reduce the success rate of attacks by 90% when HRV countermeasure has been applied.
Biometric Key Generation
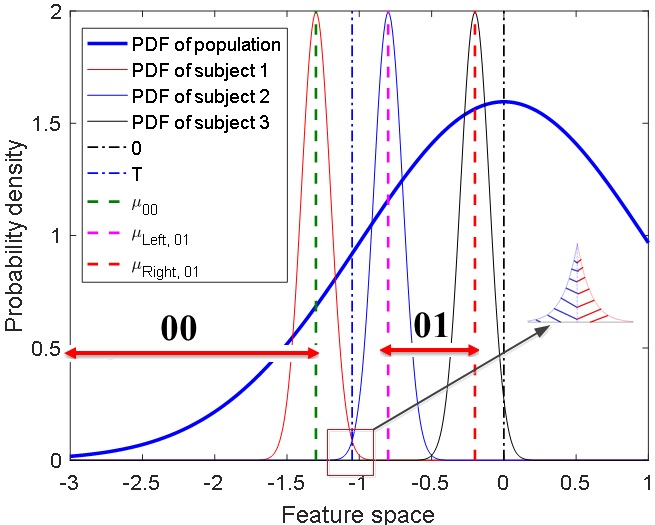
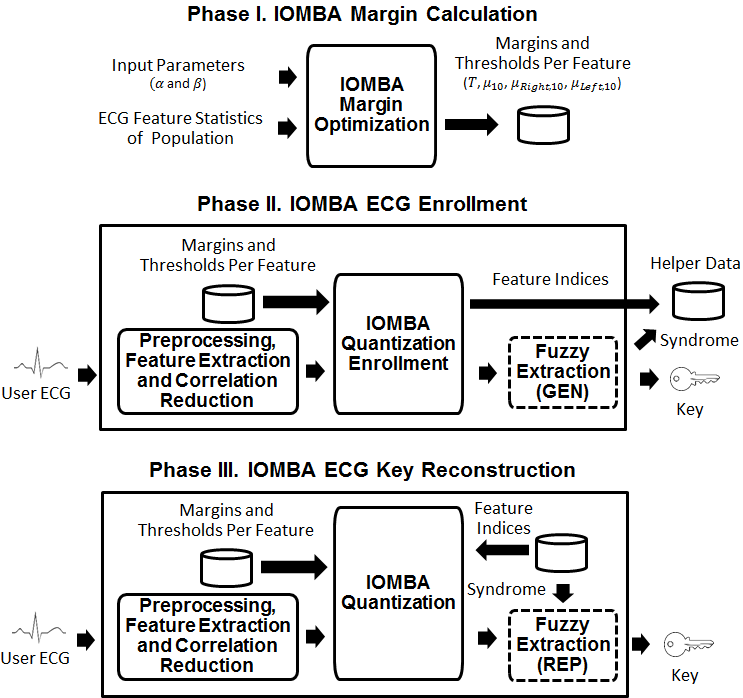
A biometric is defined as a behavioral or physiological characteristic that is used to recognize a person’s identity. In order for a biometric to be effective, it must be universal, unique for each individual in the population, and stable over time. One of the challenges associated with traditional biometrics such as fingerprints, face recognition is that they can often be lifted or captured without a person’s consent. Among the strengths of ECG in biometric recognition is its continuous property. we introduce a new promising framework Cardiovascular authentication that can generate unique, reliable, and high entropy keys with low enrollment times and denoising costs. To this end, we developed interval optimized mapping bit allocation (IOMBA), which exploits population and noise statistics in order to optimally quantize each ECG feature into one or more bits. Unlike iris or fingerprint images that can be scanned at a single point in time, the ECG signal has a constant flow that allows it to be continuously reassessed to identity a user.
Hardware Obfuscation
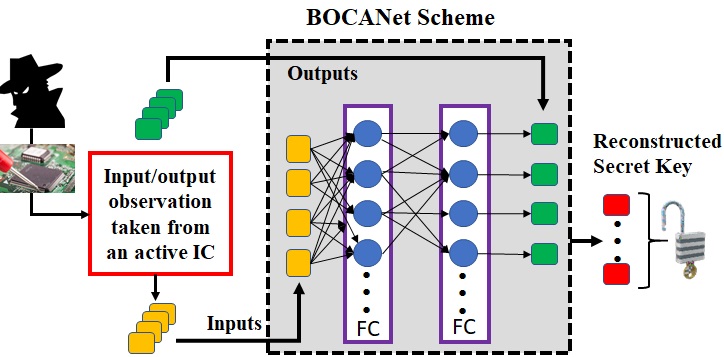
Over the past two decades, many of the leading semiconductor companies have become fabless due to the fact that the increasing costs and complexity confine them not to design, test, fabricate, and package ICs. Thus, reverse engineering is a major threat resulting in piracy and/or modification. To protect against it, hardware obfuscation is a technique that can provide sufficient security with minimal modification of the design flow. However, it is possible for an adversarial to break hardware obfuscation techniques. In this project, we propose a new attack model against logic encryption obfuscation using deep recurrent neural network (D-RNN) denoted as BOCANet: Broken obfuscated circuit attack. BOCANet incorporates D-RNN to compromise the secret key from obfuscated hardware (logic locking) an order-of-magnitude more efficiently (> 20X faster with relatively high success rate) compared to existing SAT attacks.